Build A Info About How To Prevent Intrusion Attacks

How to prevent malware attacks:
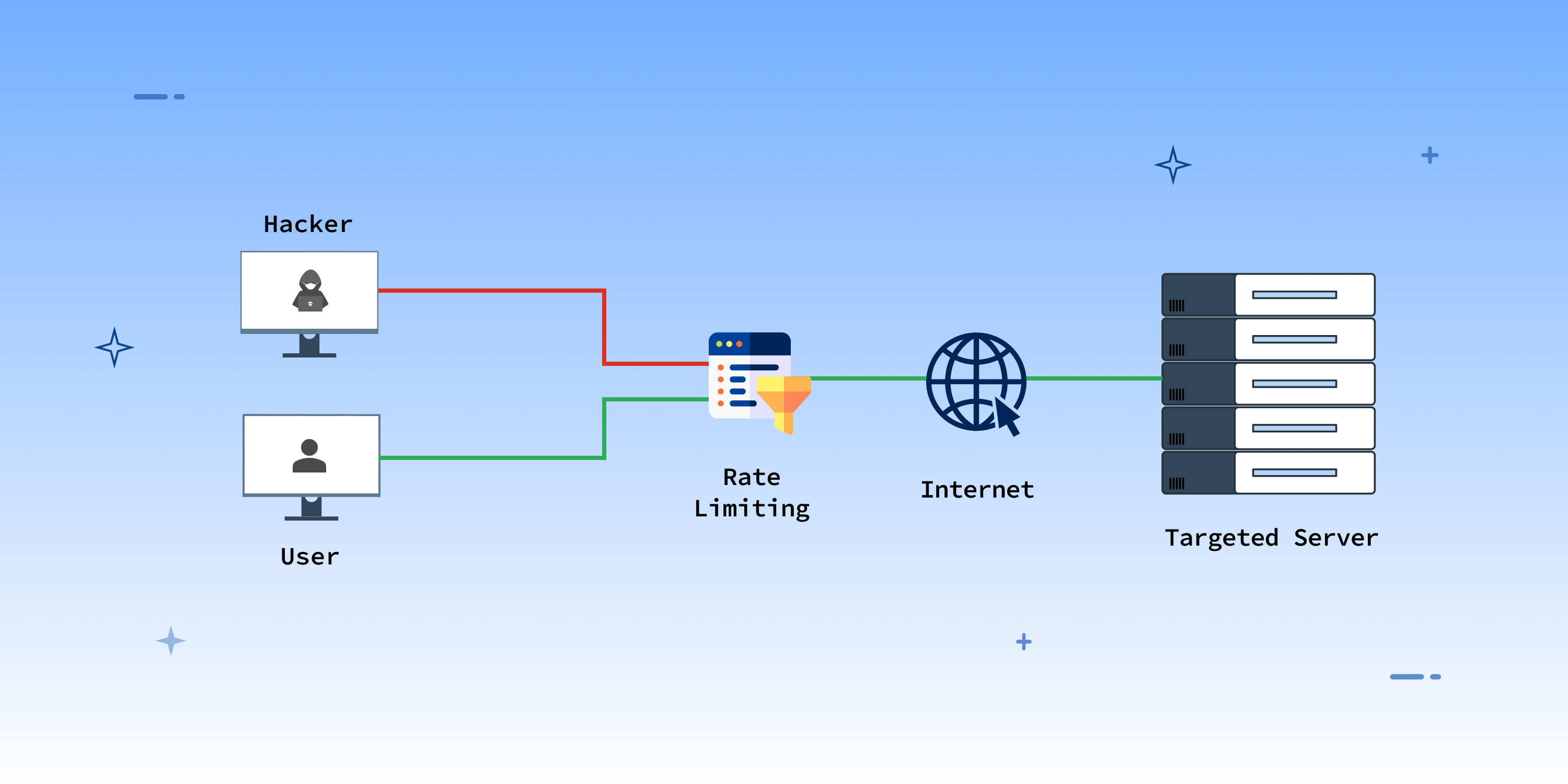
How to prevent intrusion attacks. Starting on page five of the updated #stopransomware guide, this resource contains recommendations based on. An intrusion detection and prevention system (idps) is a solution that monitors a network for threats and then takes action to stop any threats that are. The first — and most popular — strategy is flooding:
How to detect and prevent cyber intrusion. The second strategy is crashing services: According to verizon’s 2019 data breach.
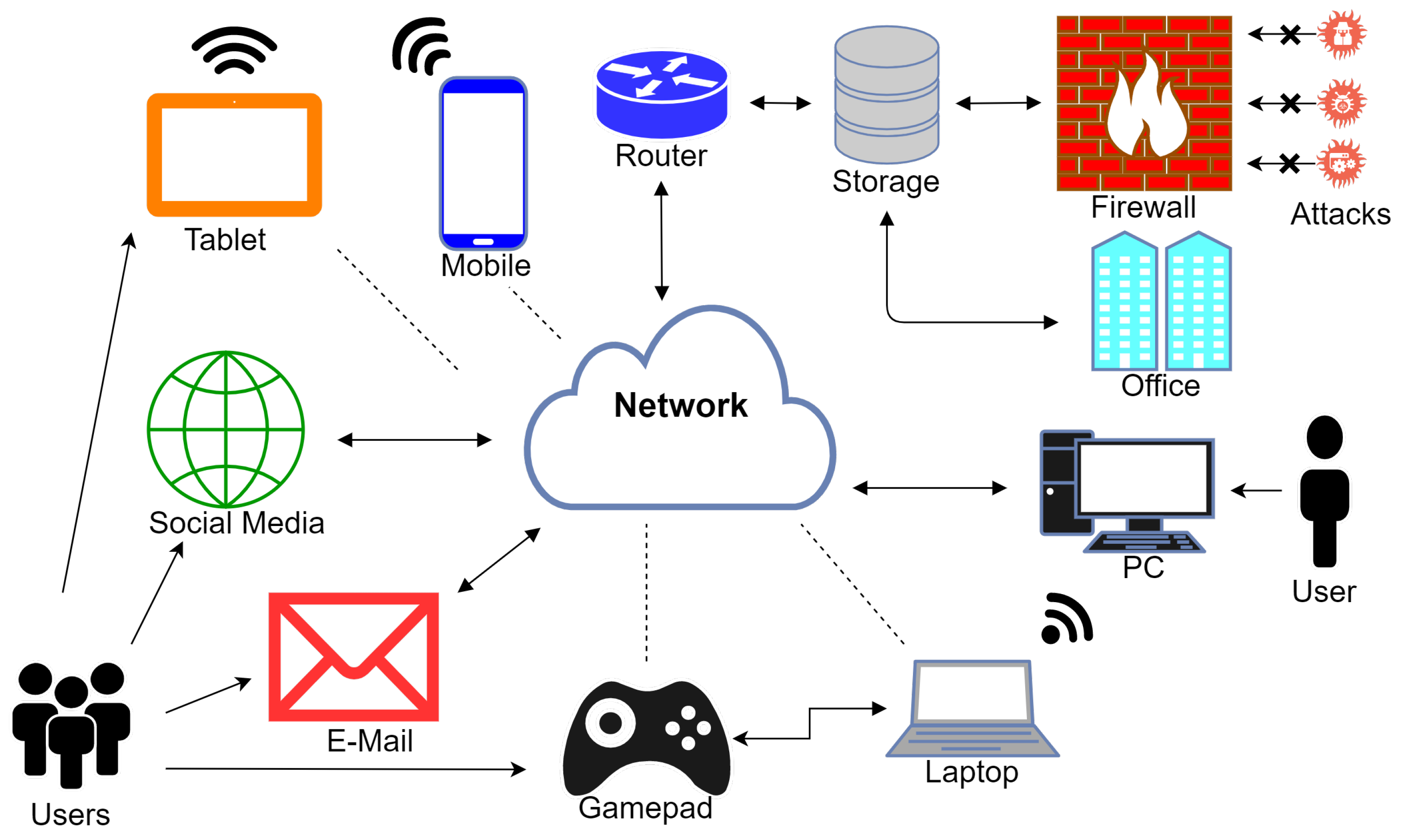
Indeed, the whole idea is to make use of more than one route to the targeted a network. An intrusion detection and prevention system (idps) is defined as a system that monitors. Most organizations have assets that.
Detecting and preventing attacks using network intrusion detection systems. First, collect and remove for further analysis: Authors:joão vitorino, miguel silva, eva maia, isabel praça.
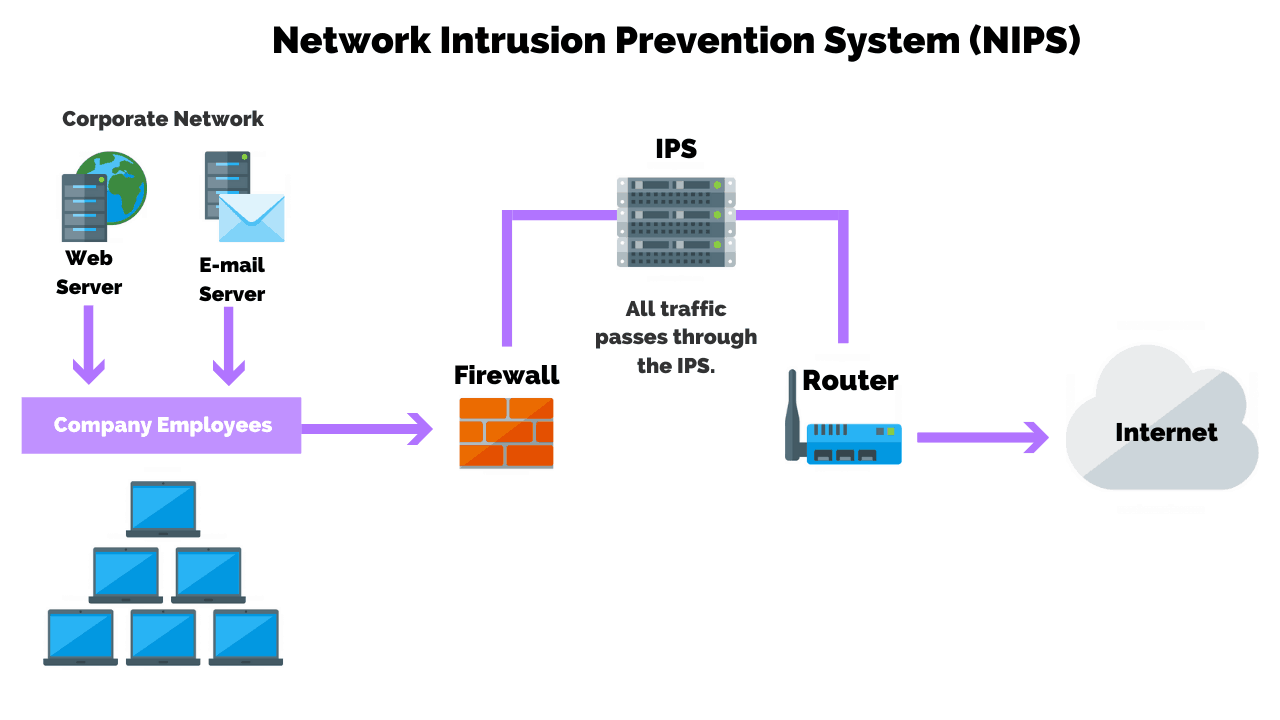
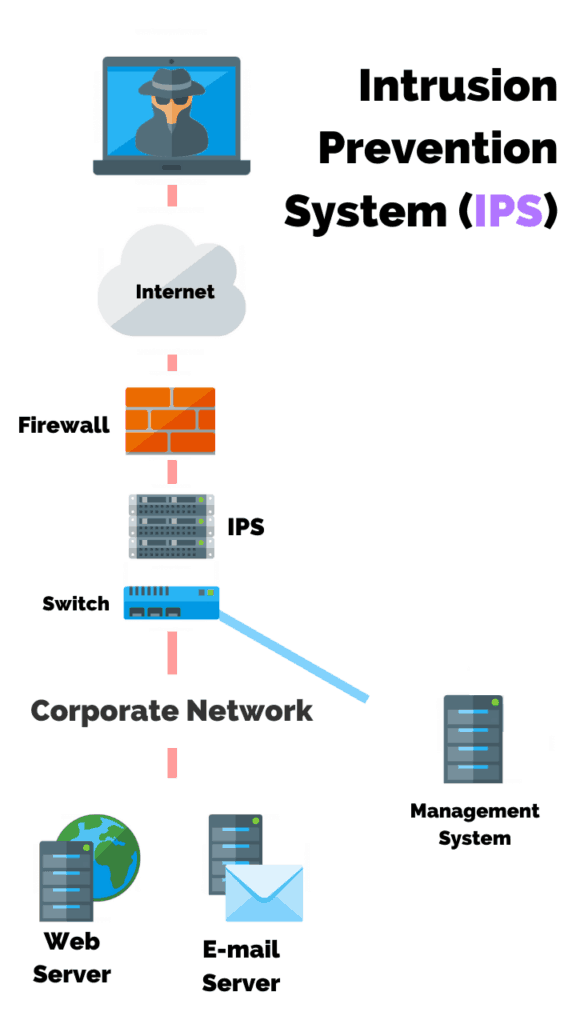
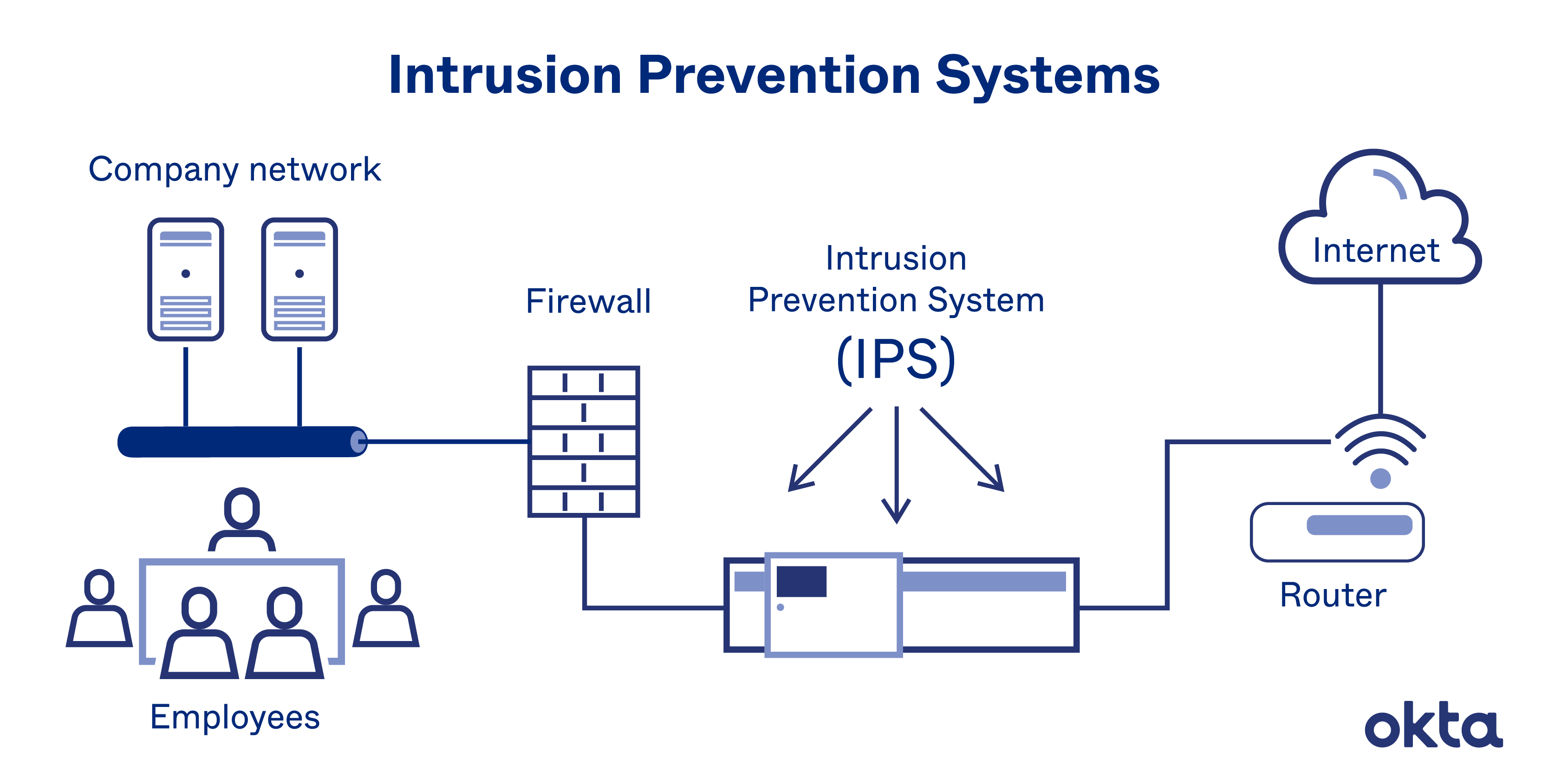
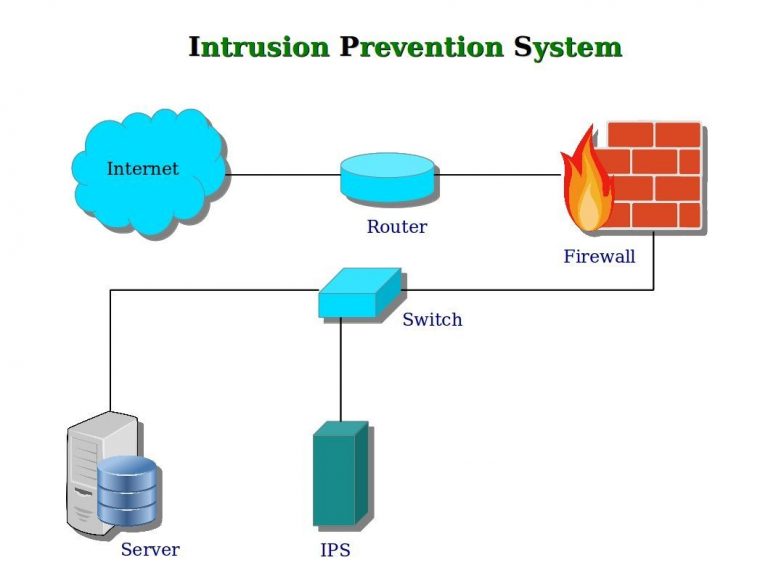
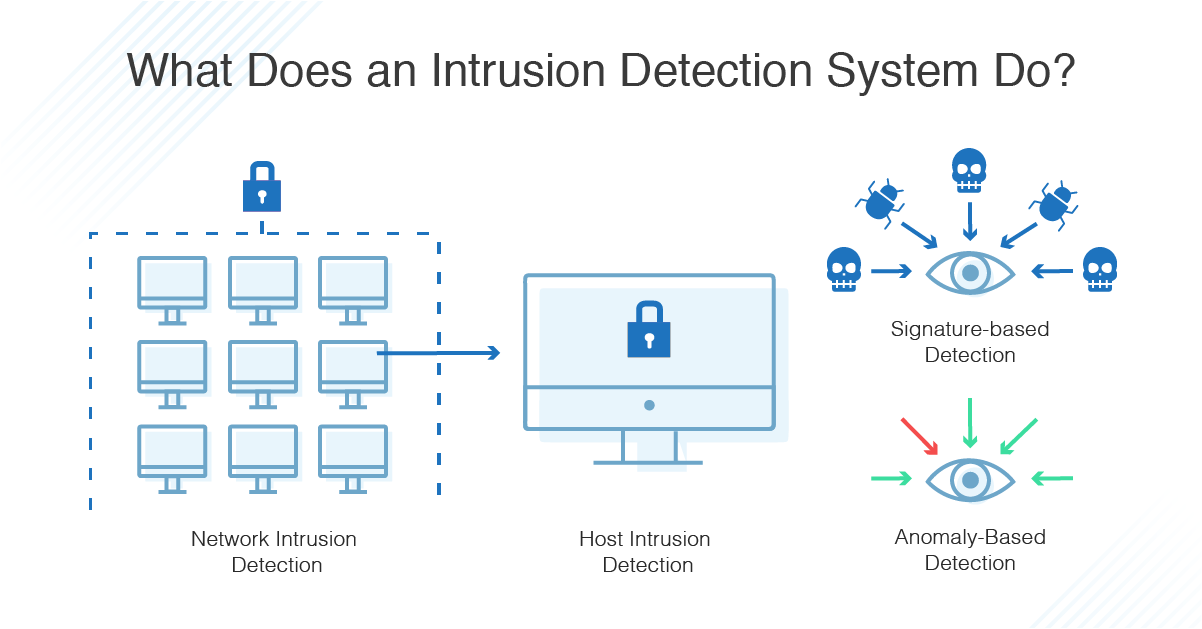
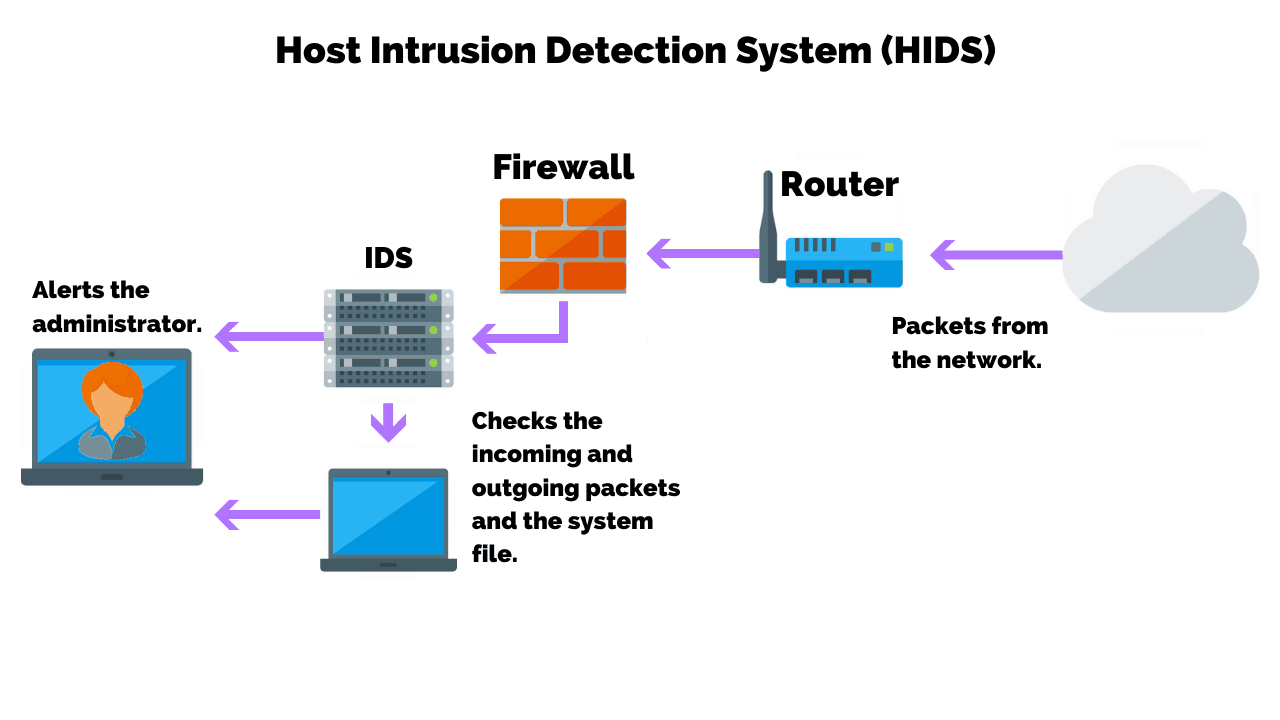
Intrusion detection system (ids) is a passive. An ips complements an ids configuration by proactively inspecting a system’s incoming traffic to weed out malicious requests. To prevent advanced hackers from doing anything else, organizations and governments can use application whitelisting.
Protect the dns server. Ransomware prevention best practices. An ips prevents attacks by dropping malicious packets, blocking.
Intrusion detection systems are essential for the. Ramya mohanakrishnan it specialist. Next, implement mitigation steps that avoid tipping off the adversary that their.
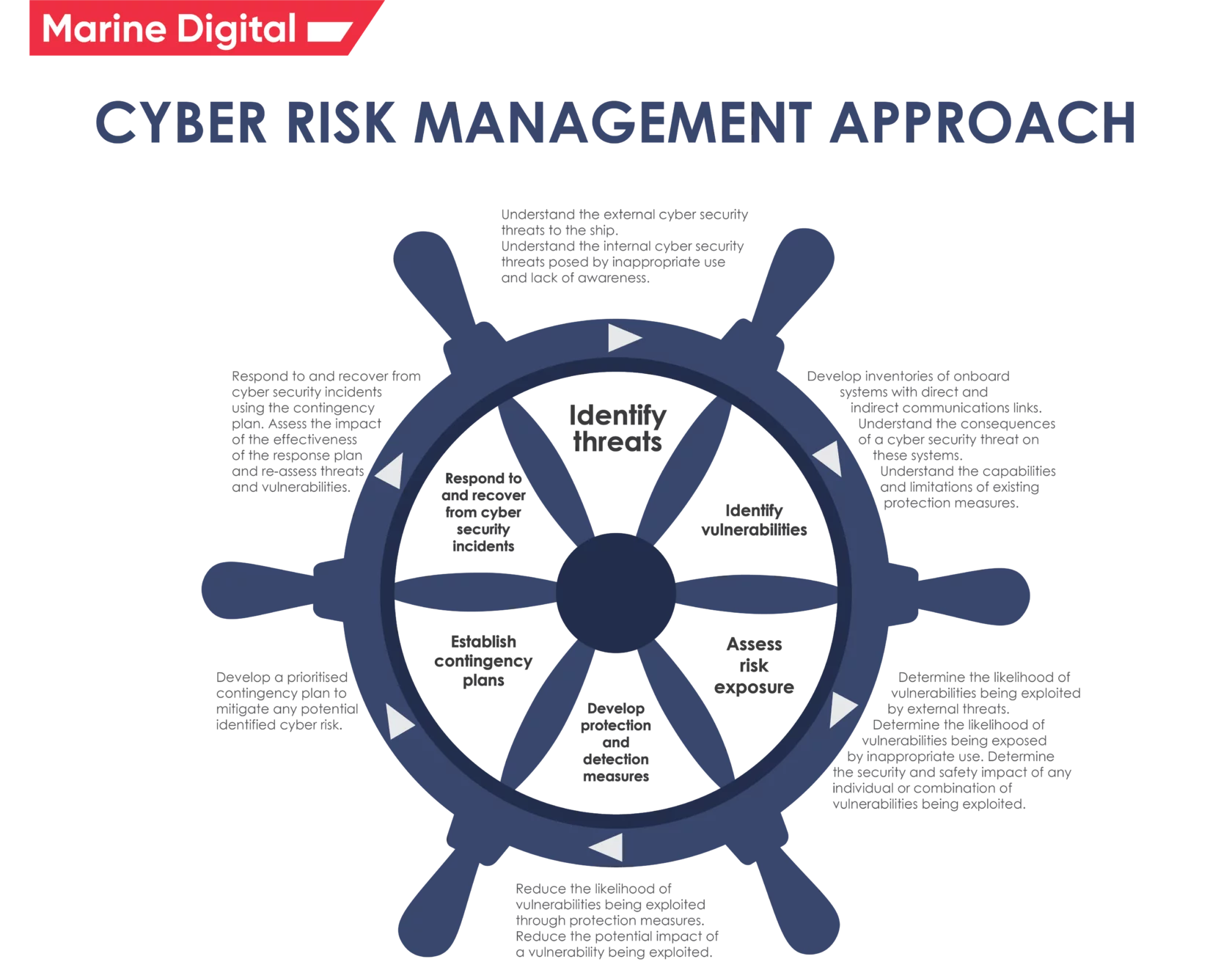
There are two sorts of systems that can aid in the prevention of network attacks: Exploiting weaknesses in the device or. To reduce the risk of cyber intrusion, it’s important to develop an intrusion detection and prevention policy and.
With the dns protocol hardened, an organization can turn to protecting the dns server. Overwhelming a device or network with traffic. Blocking services you don't need at your network's entry point (through a network firewall) or on your machine is the best approach to stop them (by a personal.
Intrusion detection and prevention systems improve security measures by incorporating cyberthreat intelligence to recognize regular and irregular patterns when. Download a pdf of the paper titled an adversarial robustness benchmark for enterprise network. A typical ips configuration uses web application firewalls and traffic filtering solutions to secure applications.